Types of Proxy HTTP, HTTPS, Socks
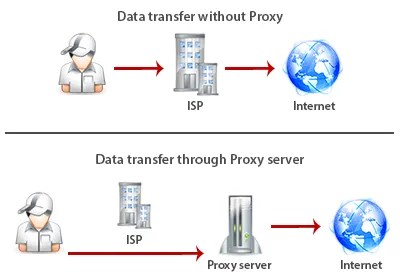
Proxy an intermediate transit web server, which is used as an intermediary between the user and the destination server.
The main purpose of a proxy is a change of IP address.
Consider the situation when a user visits Google.com through a proxy. In this case, the user sends a request to the proxy to open a website. The proxy on its behalf opens Google.com and then transmits the data to the user.
Types of proxy
Proxy servers are a few types:
- FTP proxies are used to load data to an FTP server
- CGI proxy (anonymizer) helps to open any website directly in your browser. No additional configuration is required. Most often, such proxy is presented as a website where you can enter the address of the site you want to visit
- SMTP, POP3 and IMAP proxies are used to send and receive e-mail
- HTTP and HTTPS proxies designed for web browsing
- Socks proxy sends all the data to the destination server as a client, therefore considered the most anonymous protocol
HTTP, HTTPS and Socks proxies are used more often, so consider them in detail.
HTTP proxy
HTTP proxy is the most wide-spread type of proxy. The main purpose is the organization of the work of browsers and other programs that use the TCP protocol. Standard ports 80, 8080, 3128.
How it works: The program or a browser sends a request to a proxy server for opening a particular URL resource. The proxy server receives the data from the requested resource and sends the data to your browser.
HTTP proxy allows to:
- cache downloaded files (images, pages) to increase the opening of the website speed
- restrict access to certain resources (eg, Youtube)
- filter the data. For example, instead of banners with advertising display transparent images that will not break the design of the site, but will significantly save page load time and bandwidth
- limit the connection speed
- keep logs, monitor traffic for users
Types of proxy for anonymity
HTTP proxy on anonymity are divided into the following types:
- transparent proxy declare that you are using a proxy and pass real IP address of the user in the HTTP headers. Transparent Proxy use is dangerous, since they do not provide anonymity
- anonymous proxy notify that the proxy is used, but it does not convey the real IP address of the user. Anonymous proxies can not guarantee this anonymity because the claim that the proxy is used
- elite proxy is not notify that a proxy was used and do not convey the real IP address of the user. Only elite proxies can be used for complete anonymity
HTTPS proxy
HTTPS proxy in fact it is the HTTP-proxy, the letter "S" in this case means "secure" with support of SSL connection. These proxies are used when you want to send sensitive information (eg usernames / passwords, plastic card numbers). Standard ports 80, 8080, 3128.
When using a conventional HTTP proxy all information transmitted through it can be intercepted by means of the proxy or at a lower level.
For example, all Internet service providers intercept and logged absolutely all of your activity on the Internet. These logs are stored, and the provider is reasonable proof of your actions on the Internet. Therefore, the HTTPS protocol is used for the security of personal data, while all traffic is encrypted and resistant to cracking algorithm.
How it works: proxy server connects to the resource and your traffic is encrypted. With this method there is no possibility to find out what information is passed through a proxy server (this limits the use of proxies as a filter). Also in the process of encrypting and decrypting a proxy does not participate. This deals with a client program (browser) and the target server. Thus, HTTPS proxy is engaged in passive transfer of encrypted data and does not do any processing of the transmitted information. This method of operation allows the use of HTTPS proxy to transfer virtually any TCP-protocol. That is, the HTTPS proxy can be used as POP3, SMTP, IMAP, NNTP proxy.
Socks proxy
Today Socks proxy is the most advanced data transfer protocol. Sometimes mistakenly called Socs, Sox, Soks. This protocol is designed by Dave Koblas.
Socks protocol developed for programs that do not support the use of proxy directly. Standard ports 1080, 1081.
This protocol has gone through many changes and now uses two protocol versions:
- Socks 4 supports only TCP connection
- Socks 5 supports TCP, UDP, authorization by login and password, and remote DNS-query
Socks is not engaged in moderation HTTP-header. Socks-server will transmit information through itself in its purest form. Therefore, all Socks servers are anonymous.
Socks proxy does not send information about your IP address. The website will not be able to determine the use of proxies. The connection with the website will be totally transparent, as if you were working directly with them. This web site will see the IP address of the proxy and not your real IP address.
Socks поддерживает все протоколы, включая HTTP, HTTPS, FTP.
We recommend to use Socks 5 proxy
Comparison of different types of proxy
Table comparing the different types of proxy.
| HTTP | HTTPS | Socks | |
|---|---|---|---|
| Caching pages, fast loading | |||
| Support for https (SSL) connection | |||
| Completely anonymous protocol |
Where is installed proxy
Proxy is a program that handles requests from the user to the destination server. Such a program is installed on the user's computer or server.
- Proxies are set to ordinary user computers using Trojans or viruses through botnet. The botnet - a network of infected computers controlled by the host computer. The proxy performs your requests, acting on behalf of an infected computer. This type of proxy provides maximum anonymity. Less proxy - can not be guaranteed a permanent job proxy, as installed on the remote computer.
- Proxies are configured on own servers. Such proxies are the most reliable, because the server is running all the time. Constant proxy need not be checked for validity. Less proxy - it can not ensure perfect anonymity, because it is known who owns the server and it can seize.
Paid proxies are adjusted in order to obtain material gain from the sale and often different levels of anonymity.
Free proxy
On the Internet, there are websites, which publishes free proxy. For what purpose are published free proxy? To answer this question clearly difficult. Free proxies can be used for learning how to use a proxy. Free Proxy fit you, if anonymity is not important.
Causes of Free Proxy:
- incorrect configuration of access to the proxy by the local network administrator. The network administrator has not closed access to the proxy on the Internet
- universities and schools provide access through a proxy to his university library. This proxy is listed as public
- proxy from government organizations
Using a public proxy is very dangerous. Since we already know that the proxy can cache, collect statistics on users. Accordingly, some organizations are interested in placing public proxy for the purpose of tracking users.
We do not recommend free public proxy.
How to use proxy
If your goal - it's anonymous use of the Internet, we recommend using only Socks 5 proxy.
For the purposes of data parsing, SMM, SEO and online games, you can use HTTP / HTTPS proxy.
The proxy can be configured in the browser or through a special programs.
Proxy chain
Proxy servers can be arranged in chains. In terms of anonymity and speed sufficient to use a chain of 2 proxy in different countries. These will pass sequentially through two proxies.
Remember all ISPs can log your actions and listen to your traffic through a proxy.
We recommend using VPN + 2 proxy to ensure your anonymity.
