How to get to know if a VPN service keeps logs
Presently, computers and phones can spy users, thus, security and anonymity on the Internet is very important for all people.
Using a VPN service without logging allows fully solving the problem of anonymity. To start with – let us find out what VPN service logs are.
What are VPN server logs?
Logs are any entries helping to identify each client individually. For example, PPTP VPN has no built-in log off function. A log is written to the standard journal of operating system logs. A PPTP VPN server log is presented on the picture below, taken from the Internet.
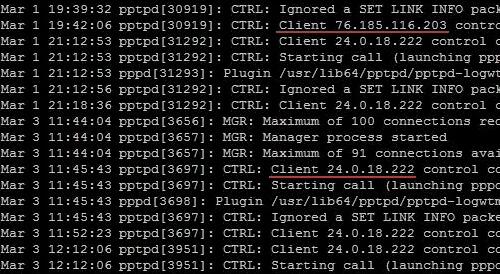
Standard PPTP and OpenVPN server log contains connection time, real IP address of a client, as well as a set of instructions showing connection status. The presence of real client IP addresses and connection times allows to accurately identifying each client.
The following parameters can be used as client identification on the server:
- real client IP address, which is issued by the ISP;
- internal customer number in the system – a unique customer ID in the system;
- browser settings, operating system, and connection time – all data can be taken from the user's browser, traffic analyzer, etc.
- internal IP address of the client when connecting to VPN - the IP address can be a kind of 10.0... or 192.168... and is used to forward traffic within the VPN network;
- external client IP address - it is this IP address will be displayed on the Internet sites.
If there are controls that allow blocking a specific user in the entire system, this means that this service is not anonymous and keeps logs.
What is better – shared or dedicated IP address?
We are often asked what IP address is better to use: shared IP for all users or dedicated IP for each client?
Since the unique dedicated IP address for each client may be a user ID in the system, it is safer to use a common IP address for VPN server.
An abuse is sent to a server owner with an indication of the IP address and the time of attack. If a service keeps logs, then these two parameters of the client can be used to accurately calculate find a client using a dedicated IP address for each client.
We recommend that you use a static (permanent) public IP address.
Now we know what server logs are and which IP address is better to use. Let's switch to the list of questions, getting answers to that, you will exactly know whether the VPN service keeps logs and if it if provides anonymous services.
Here is a list of questions to determine if a VPN service is anonymous
The most commonly asked question that our clients address our technical support is whether your VPN service keeps logs?
This is not surprising. Now, many services on home pages of their sites indicate that they provide anonymous VPN. But in "Terms and Conditions" with the fine print they report about reserving the right to record users data for their own safety. Thus, there is a reasonable question: can such a service be considered anonymous?
We have assembled a list of questions, which can accurately help you to understand whether a VPN service keeps logs and can be considered anonymous.
You can always ask these questions to customer support (or sales department) and analyze the answers. You can simply copy these questions from here.
We recommend using a trusted anonymous data channel (anonymous VPN + TOR + proxy), as some services may cooperate with the police. All questions are related to information security, thus, you may be followed, believing that you are a hacker.
How should you ask questions?
You should ask 1 question in a letter and wait for an answer. Then you can send the second question, and so on. If you write all questions at once, you will never get honest answers.
Question 1: Where is your office?
This question is necessary to ask to understand a company is officially registered and whether it has an office. Or it is a ghost company that has a website only.
POSSIBLE ANSWER 1: Our office is located in a certain country, and has a state registration.
This is bad, because the police can send a request to the legal office of the company and it will be obliged to give the police response according to the law. By law, all companies are required to keep logs and monitor their clients’ activities. If they do not do in such a way, the entire legal responsibility for the customers’ activities falls on them. All officially registered companies with formal offices are required to keep logs and cannot provide anonymous services. As a rule, office address and registration numbers of the company are shown on the web site.
POSSIBLE ANSWER 2: We have a website only. This option is better, as your email sent to customer support does not entail legal consequences.
POSSIBLE ANSWER 3: Our company is registered in offshore zones, on the Cayman Islands or the islands, where there are only trees and coconuts :) This answer is often given to give the company status and credibility. But it is actually the answer 2. There are times when a company is really registered in offshore countries. This is also bad, because it is possible to send an official legal request to this country, and the company will be obliged to give the official answer according to the law of that country.
Question 2. Does your service keep logs?
POSSIBLE ANSWER 1: Yes, we keep logs.
After such an answer no more questions should be asked. All becomes clear. You can only thank customer support for being honest :)
POSSIBLE ANSWER 2: We collect some statistics on the use of our services. Go to Question 3.
POSSIBLE ANSWER 3: No, we do not keep logs. Go to Question 4.
Question 3: What kind of statistics do you collect (what data)?
POSSIBLE ANSWER 1: personal data (such as: Email, connection time, browser version, operating system, etc.).
In this case, it is possible to identify a user. Most likely that such a service keeps logs and it is not anonymous. Go to Question 4, to check it out.
POSSIBLE ANSWER 2: We use Google Analytics for statistics of visits to our site. There is nothing bad in it, as Google Analytics only collects statistics on site visits. Go to Question 4.
Question 4: You have said that you do not keep logs. If I spam or attack websites using your VPN, will you block my account?
POSSIBLE ANSWER 1: No, we will not block your account, but if there are many abuses, we will block access to the site using the VPN, from which abuses come. Thus, your account will work, but you will not be able to enter this site using our VPN. Thus, this is an anonymous VPN service, and does not keep logs.
POSSIBLE ANSWER 2: Yes, we will block. Still, we have a system that allows us turning off the logs on the server, but yet identifying prohibited activities. Consequently, your account will be blocked by the system. Go to Question 5.
Question 5: How does your security system work?
POSSIBLE ANSWER 1: We cannot tell you, since this is our secret.
This answer says only one thing - this service keeps logs, and is not anonymous. Because, if there was such a magical system, it would be possible to tell about it everyone all and be proud of it. Unfortunately, these are no miracles.
POSSIBLE ANSWER 2: More often after such questions technical support (sales department) stops answering your questions. It also says that the service keeps logs and is not anonymous.
THE LAST QUESTION: Are you ready to check it on yourself?
If after getting answers to all questions, you feel that the service is anonymous and does not keep logs, you can try it by yourself. You should make all further actions at your own risk, as you will be responsible for your actions. We do not recommend you doing so. But such actions will directly answer your question whether the VPN service keeps logs.
Use plenty of ways to protect your activity (anonymous VPN + TOR + proxy). We will tell you about the ideal protection in the future articles. The bottom line is to connect to the VPN server in this service and try to perform prohibited acts. If your account is blocked, then it keeps logs the service is not anonymous. Once again we remind you that we do not recommend doing so, but how else can you find out the truth?
How does our anonymous VPN service work without logs?

If any client performs prohibited activities using the VPN server, thus, the only purpose of the service is to stop these actions.
The VPN service does not care which client does so.
You can filter the traffic by using different programs (for example: tcpdump) and understand which site is being accessed. Or you can take a site listed in abuse and simply block access to it. After it, no client can enter this site using the VPN server. The attack is resolved and there is no sense to find a client who performed this attack.
This is just a small example of how the anonymous VPN service works. But it clearly shows that there is no need to block a client, only if the service is not an official company with an office, where an official request from the police can be addressed.
We are often asked why we have such a price for VPN service. Currently, there are many VPN services that provide services for $ 5-10 per month. Let's look at this in details.
Phenomenon – a VPN service for $ 5
What does get a client that uses a low-cost service receive? Many people think that they buy a low-cost safety. But there is no cheap security.
Winston Churchill once said, "You should pay for security or you will face the day of reckoning".
Disadvantages of cheap VPN:
- Cheap or free VPN can be a lure of police. This VPN cannot provide anonymous services, and vice versa can collect data about you.
- Many companies specifically use a dynamic IP address so that you can identify each client on time of connection and IP address. Each client receives a unique and dedicated IP address when he connects.
- Cheapness is achieved by purchasing multiple servers and binding to them many packages of IP addresses from different countries. As a consequence, it uses of Google DNS on all servers. Accordingly, your DNS will always be shown as the United States, and you will change the exit points, for example, in Germany or Malaysia.
- Drop of the connection speed, since on 1 server there are always more clients.
- Recommendation to use an unreliable PPTP connection, because it is easily to set it up. It is supported by default by all operating systems.
- No OpenVPN configs to manually configure the connection through a formal application OpenVPN with an open source.
We recommend using a cheap VPN service, if you just need to change your IP address to unlock services which are not available in your country (e.g., Facebook, Twitter, and Google Disk). It is only when you do not need anonymity. Most major VPN companies keep logs on their servers.
Why are there so few anonymous VPN services without logging?
An anonymous VPN service, that keeps no logs, cannot find out which client breaks the rules. This is the core problem, as a single unscrupulous client can interfere with the whole service.
Only the development of a protection system against abuses can disable VPN server clients break the rules (for example: to send spam, perform attacks, scan ports servers, etc.). Typically, services are afraid of abuses and easier to abandon clients, than to answer abuses.
We often say a word “abuse”. Let's take a closer look at what it is.
What is an abuse?
When we say “an abuse” we mean the complaint. When your site is being attacked, you can write a complaint to the IP address owner. An abuse usually comes in email. The site, which was attacked by the VPN server, sends a complaint to the IP address owner from which the attack was performed. In most cases the IP address owner is an organization, and it resends such an abuse to the server owner. Now it is his turn to take certain actions to stop this attack.
Currently, there already exist many automatic tracking systems for compliance with the copyright in the Internet. For example, a user downloaded a torrent file with the famous film by Paramount Pictures Company on a torrent tracker. The system automatically finds the client IP address that made it, and also automatically sends an abuse to the IP address owner from which an illegal film version was downloaded. A similar situation is with e-books copies.
Here is an abuse example showing an attack on a third party server (all images are taken from the Internet). This abuse contains the external IP address of the attacker, time of the attack and the website, which was actually attacked.
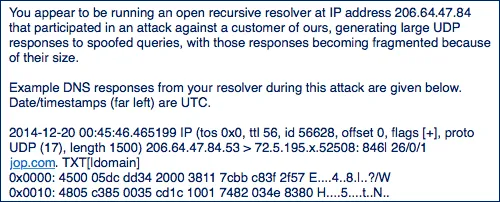
How do we process abuses?
In fact, there is nothing bad in abuses. This is just a signal that you need to take some action. In case of torrent trackers, we just block the resource. A client will not be able to use the VPN specified server for downloading the movie. There is a list of servers on our service that you can use to download torrent files. These VPN servers are located in data centers, which are loyal to such operations.
We do not process requests. Our servers do not keep logs, and therefore there is no sense to cooperate. We have no data to identify a client. If we receive requests concerning attacks on a site, then we simply block an access to this site, similar to torrent trackers.
What happens if I do not respond to an abuse?
We need to work with abuses. The vital factor for data center is to get the answer that we will eliminate the cause of the abuse. And the most important thing is really to eliminate it. If you ignore an abuse, the data center will immediately disable the server. We provide services to our clients and do not worry them about nothing. And it is our job to answer an abuse. We often receive abuses, but our clients do not even know about it.
Is it possible to completely disable logging?
Internet users often ask whether it is possible to completely disable logging.
There are operating systems that can do this. It is Linux (and all its variants).
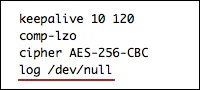
For example, the command «log/dev/null» on Linux completely removes all the logs of OpenVPN service. Owing to the settings, you can completely disable the logging of any connections to the OpenVPN server.
Our job is to ensure the safety of our clients

We use additional means of anonymity. We create action anonymizing on the server itself. Thanks to this the highest level of safety and anonymity while working with our service is achieved.
Since the beginning of our work (in 2006), there is no case, when a client suffered by our actions.
And there is another theme in terms of anonymity. Is it true that there are systems that can monitor user activity on the Internet?
User tracking systems
There are traffic sniffing and user tracking systems on the Internet via a telephone, fax, wireless and radio connections. Such systems are installed in all data centers in the world and are located in front of the equipment of the data center or Internet service provider. They always have an access to all data and there is no need to write official letters to ISPs. The country's security service by itself may view all the data it needs without any permission from either Internet service provider or a user. Now even the ISP does not know which user is being tracked.
For example, Solera system is used in most of the CIS countries, Europe and the United States. In Russia there is SORM system. SORM-1 was introduced in 1996 for the wiretaps. SORM-2 was implemented in 2000, and its functionality has been extended to the users tracking on the Internet. And SORM-3 has been implemented already.
Here is a list of what Solera can do:
- binding network packets to user identifiers;
- sorting and organizing the selection of IP address data, e-mail logins, social networks, instant messaging services, phone number or a subscriber location;
User tracking system is implemented on all operators in the world. Thus, the system is able to track users by IP address, social networks, unique identifiers, browser, and phone number. Thus, there is an important question, whether to use a VPN and other ways of protection, if we are being constantly tracked.
Why should we use a VPN, if Solera track us?
At the moment, a system cannot decrypt the traffic. And the only recommendation to such systems manufacturers of how to avoid it is to download a virus that would steal data from clients’ computer, or get the encryption from user itself by any physical means :)
Thus, the use of VPN helps solving the problem of tracking. The second important factor is that you need to use a VPN together with other methods of protection to make your Internet activity safe and anonymous.
I need anonymous VPN without logs
