What is Tor and how to use it
TOR (abbreviated from The Onion Router) – is a network of proxy servers which allow to install an anonymous network connections. The technology involves anonymous data can be used to browse the web, send email and instant messages.

Each data packet passes through 3 random Tor proxies. Such proxies are called nodes.
There are several types of Tor nodes:
- entry nodes are used for making the connection from the user, data encryption and forwarding to the next node
- intermediate nodes need to route traffic between the input and output nodes
- output nodes transmit data over the internet. Your IP address will belong to the output node
Below is the statistics - 10 countries which the most active use of the Tor network. Statistics taken from the official website of the Tor Project.

How Tor network works
The user runs the Tor client on your computer. Tor client downloads a list of Tor nodes.
Green arrows - the data transmission is encrypted.

Data is encrypted sequentially three keys before sending. The data packet is sent to the entry node of the Tor network. The entry node decrypts the "top layer" cipher and learns the next node to send a data packet. Intermediate and output nodes are also coming. The analogy of how clean the onion in layers.
Software is a Socks interface. Therefore, all programs able to work through the Socks protocol, can operate through Tor network.
Green arrows - the data transmission is encrypted.
Red arrows - unencrypted data.
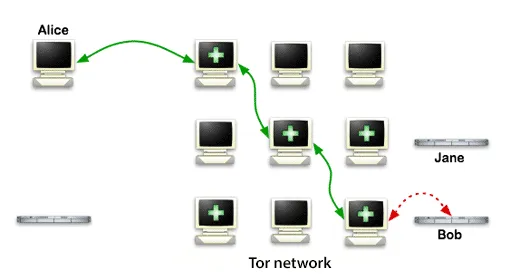
If you use Tor for a while, you will notice that the output IP address changes periodically. This is due to the random change of nodes in Tor network.
Due to the periodic change of the Tor network nodes is achieved by anonymous.
Green arrows - the data transmission is encrypted.
Red arrows - unencrypted data.
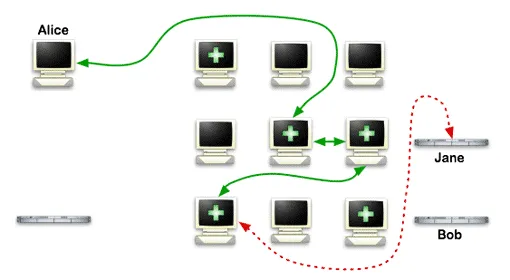
Anonymous hidden services
Tor allows to provide anonymity to servers. Access hidden server is only possible when using a Tor client. Such hidden service will work through special pseudo-top-level domains .onion. The Tor network recognizes these domains and redirects the traffic within its network.
Domains .onion can not be blocked by the ISP as it is a pseudo-domain, and access to it is only possible through the Tor network.
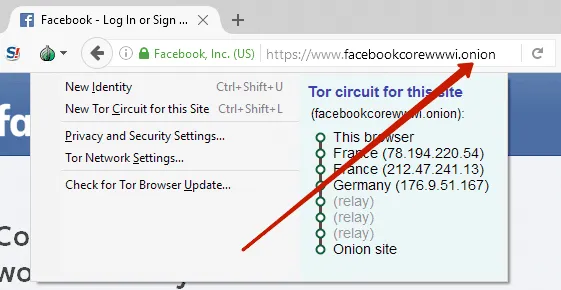
Why use Tor
Tor can be used for different purposes, but the general sense - it is a safe and anonymous use of the Internet.
Who uses Tor:
- journalists to communicate with informants and anonymous data transfer. Edward Snowden admitted to using Tor for the transmission of classified information to the Washington Post and the Guardian.
- companies to communicate with their employees on business trips
- military to transmit confidential data
- writers at anonymous blogs
Pros of Tor network
Cons of Tor network
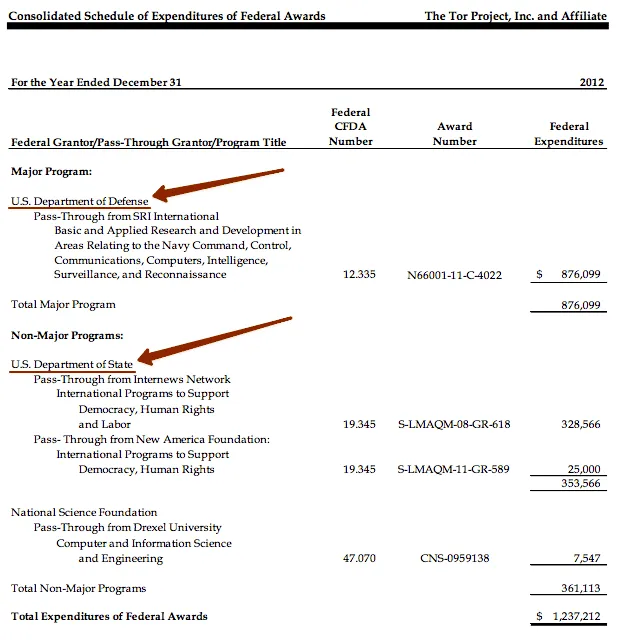
In 2012, 60% of donations for the Tor project has been done by the U.S. Department of Defense and the U.S. Department of State. It was written in the newspaper Washington Post.
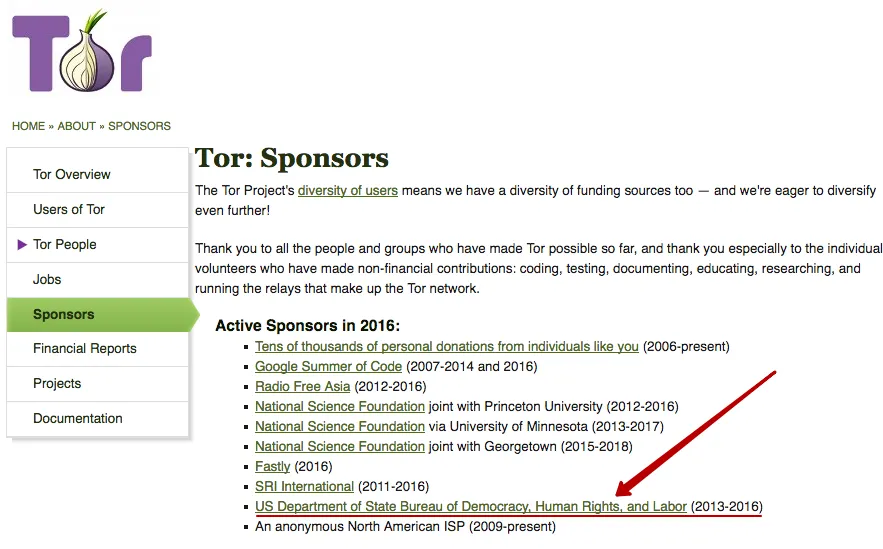
Screenshot of the report on the money from sponsors for the 2012 year. This report can be viewed on the Tor Project website.
On the website can be found the list of Tor sponsors.
For 2012 year the above sponsors are not specified. And from 2013 to 2016 U.S. Department of State (Bureau of Democracy, Human Rights and Labor) was as sponsor. At the same time on the site ceased to publish reports on the amounts of money received from sponsors.
The U.S. Department of State and the U.S. Department of Defense are customers of PRISM program. Edward Snowden gave classified information to the Washington Post and Guardian and declassified program PRISM, which carries a total surveillance of users of the Internet around the world. Large U.S. corporations (Apple, Google, Microsoft and others) through the courts are obliged to cooperate with the developers of PRISM program.
This does not inspire confidence on which side works Tor Project.
Do I need to use Tor?
Each user himself decides to use the Tor network or not. Now that you know all the pros and cons of the Tor network.
We do not recommend using a Tor network as one means of anonymity. To feel secure an integrated approach to anonymity. Use several different technologies together with Tor like onion skins. For example: VPN + Tor + Socks, SSH or a Dedicated Server.
How to set up Tor Browser
Download Tor Browser only from the official site torproject.org.
Be careful! There are sites that mimic the Tor Project website. For example, the site torprojectS.org (added the letter S at the end) is trying to install on your computer a trojan. Do not download Tor Browser on third-party sites.
By the way Tor Browser is made based on the Mozilla Firefox browser, since it is the only browser able to work independently with Socks connection without an operating system.
Download Tor Browser from torproject.org
After installing Tor Browser is fully operational. Below is a screenshot from the official website.
Recommended use Tor Browser
- do not install additional plug-ins, as it is likely to install a plugin that will give your actual location. All the necessary plug-ins are already installed for anonymity.
- do not open the documents (eg, PDF and DOC) while you are online. In such files can be embedded macros that have requested access to the Internet directly from the program, bypassing the Tor network. This compromise the your real IP address.
- do not download torrents on the Tor network, as it will increase the load on the network. Torrent program are arranged so that they always get access directly to the Internet, and do not consider the proxy settings. It can compromise your real IP address.
- use the https connection is always. This connection will ensure the security of data transmission.
Tor Browser Main Window.
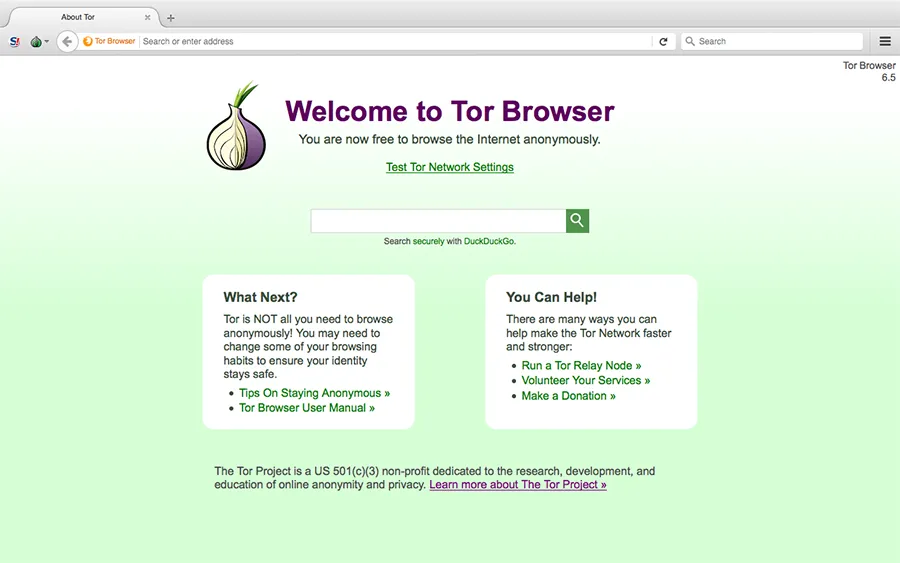
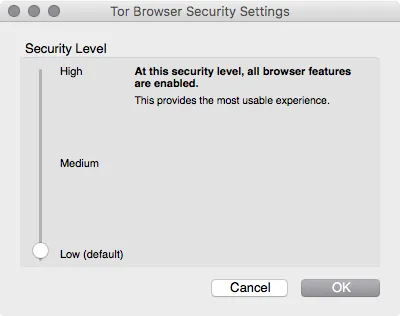
Click Security Settings.
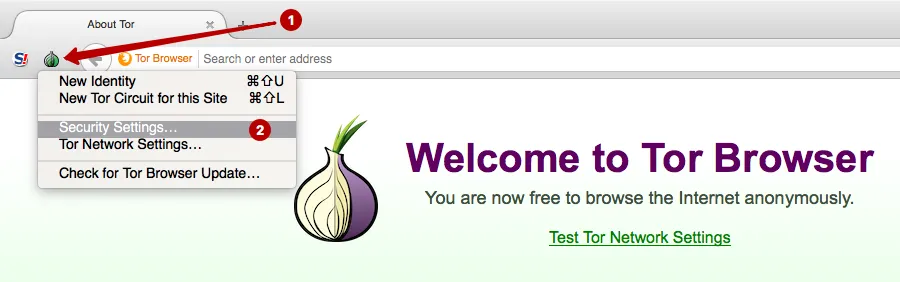
Set the security level:
- Low (default) – Standard security.
- Medium – Javascript is disabled on sites that do not support https. HTML5 video and audio is triggered by clicking through the NoScript plug-in
- High – Javascript is disabled on all websites. HTML5 video and audio is triggered by clicking through the NoScript plugin. Not allowed for loading certain types of images, fonts and icons
Suitable for most users. Web sites are opened correctly and nothing is blocked.
Since most Web sites use Javascript is, therefore, to view websites in High mode is problematic, since the content is hidden. We recommend this mode when you want to read an article on some website, it is not necessary in this case to authenticate online.
Tor Browser is ready for use, and you can immediately begin to surf anonymously.
Note that using this setting only Tor Browser uses the Tor network. All other programs are using a direct connection to the Internet and send your real IP address.
What to do with the programs that are not able to work directly with the Socks protocol? For example, e-mail clients, and other browsers, instant messaging programs, etc. We recommend the use of Proxifier to redirect traffic of such programs in the Tor network.
Setting Proxifier through the Tor network
Proxifier program can:
- redirect traffic from all of the operating system software through a proxy (including e-mail clients, browsers, instant messaging programs)
- create proxy chains
- use the DNS server from the proxy, hiding the real DNS of ISP
- supports http and socks proxy
Download Proxifier for Windows Download Proxifier for macOS
Home page of official site Proxifier.
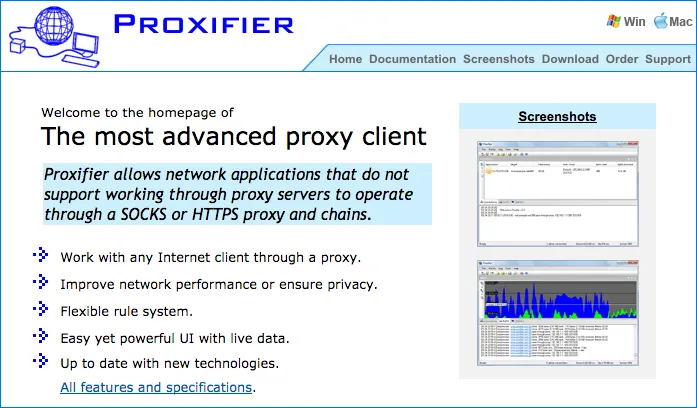
Install the program Proxifier. This program is able to collect the traffic from operating system and flowing through a certain proxy server.
To configure Proxifier need to learn use the Tor network port. Go to the Preferences in Tor Browser.
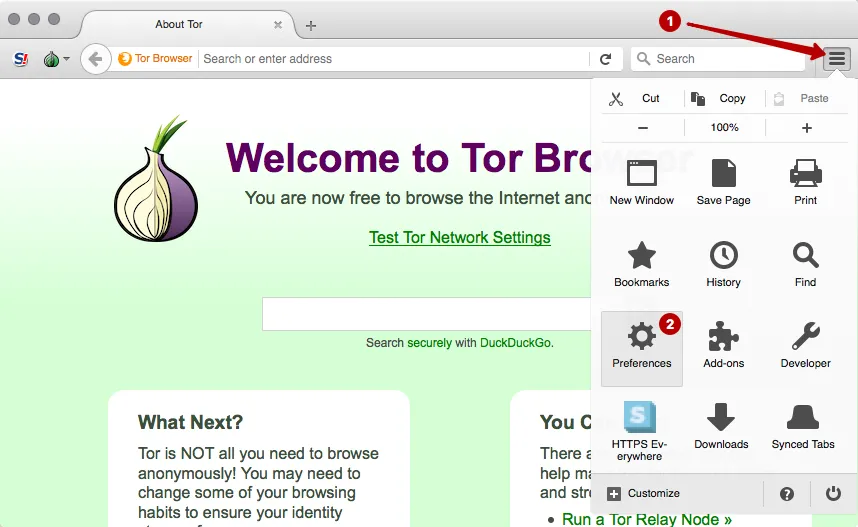
Select the Network Settings.
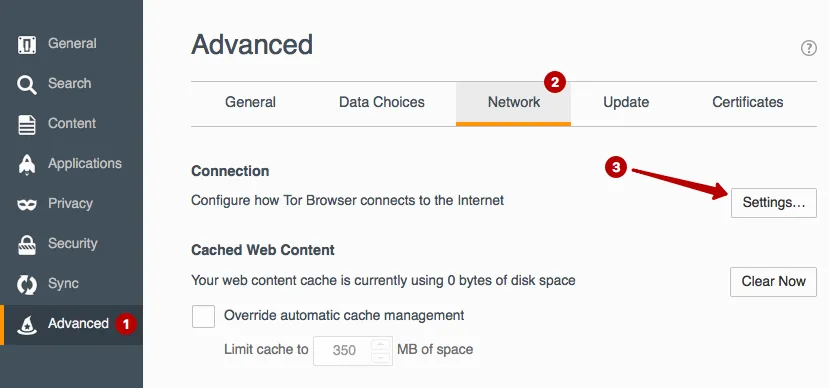
See use the local IP address and port of the Tor network connection. These data must be inserted in the program Proxifier to the entire operating system, traffic was held in the Tor network. In this example, 127.0.0.1 and port 9150.
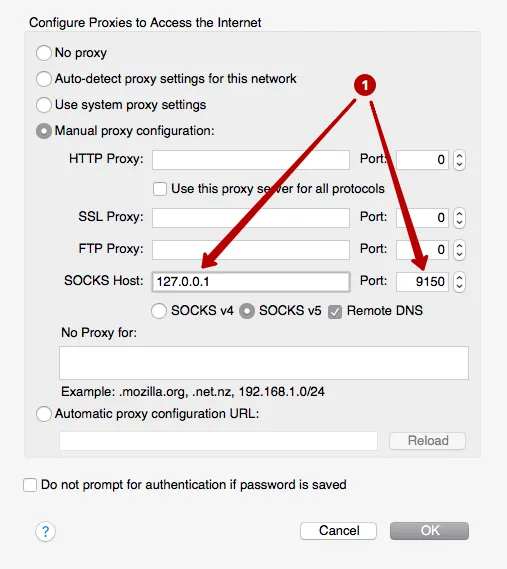
Run app Proxifier.
ATTENTION! It is important first to start Tor Browser and wait until the main window appears. And only after that start the program Proxifier.
Click on the Proxies button.
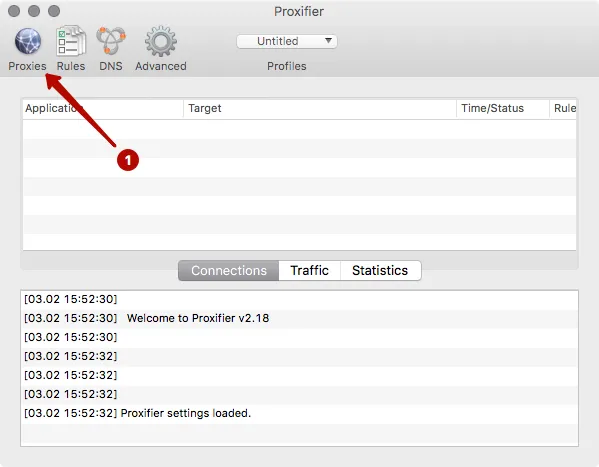
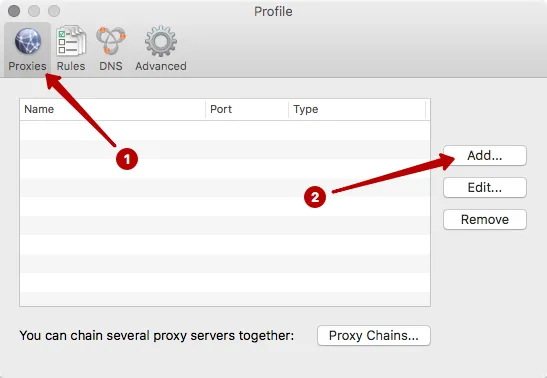
Click to Add.
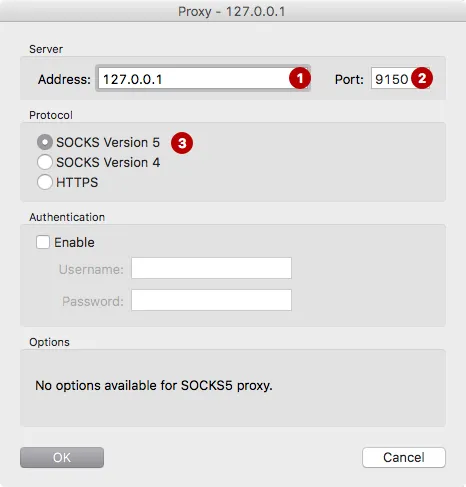
Enter IP address and port. In our example: 127.0.0.1 and port 9150.
Click Yes - agree to use proxy by default.
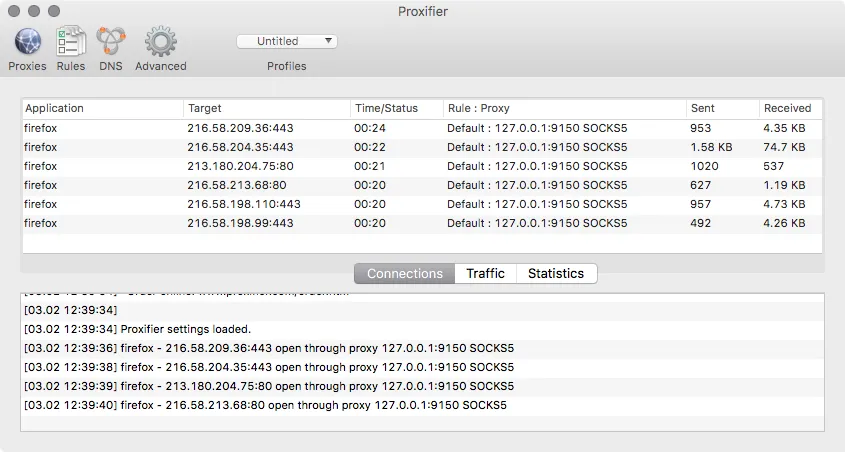
Open any browser or email program. In the program Proxifier you will see a list of connection through the Tor network. In any browser you can check your IP address and to make sure that will show the IP address of the Tor network, and not your real IP address.
If something does not work, close the Tor Browser and Proxifier. And then start the Tor Browser and wait for the main window. Only then run Proxifier. No additional configuration is not necessary to do. All traffic will automatically go through the Tor network. Close the program Proxifier, to reclaim your real IP address.
Do you need VPN?
Try our anonymous VPN without logs
We guarantee to refund within 7 days after purchase
