Comparison of the best TOP-5 VPN services
Now in the world several hundred sites offer VPN subscriptions. An ordinary user is very difficult to understand what criteria should choose the best VPN service.
Our team has been dealing with anonymity and Internet security since 2006. We have written over 200 publications on the subject of anonymity on the Internet. During this time we have accumulated vast experience in this area.
We analyzed more than 50 leading VPN services in the world and made a list of the best TOP 5 VPN services in terms of anonymity and indirect parameters that can show your real location.
If the table is not shown completely, scroll through the table to the right.
good bad information
TheSafety - the best anonymous VPN service in the world
TheSafety service has a maximum level of anonymity, protects many indirect parameters by which you can determine your real location. Other services are also highly appreciated by us, but they "tell" that a VPN connection is used.
How we compared VPN services
We selected the most important parameters that affect the anonymity of the VPN connection.
No logs
If the VPN service keeps logs, then you can not talk about anonymity. Using the logs, you can find out which sites the user visited and from which IP address. Thus, the logs show your real location if the user connects to the VPN directly through an Internet provider.
There are 2 ways to find out if the VPN service is logging.
- Read on website (ask Technical Support)
- Ask some questions that clearly show whether the VPN service is logging in reality
It is written on all studied sites that logs are not recorded.
But is it really?
Ask all services such a question:
I plan to send spam over a VPN connection. Will you terminate my account in this case? Or is it allowed on your service?
TheSafety, Cyberghost, PrivateVPN - answered the question about logs quickly.
NordVPN and ExpressVPN - asked many details, answered for a long time.
As a result, all the VPN services being investigated answered that we cannot terminate your account, because we do not keep logs and do not collect any information.
Kill Switch function
This feature helps to block the Internet connection if the VPN connection is lost. This is a really convenient feature and a guarantee of anonymity.

VPN fingerprints
VPN connection has its own labels, which can tell whether the VPN connection is used.
Such tags include MTU parameters, detection of the presence of a tunnel, open ports.
To perform such checks, you need to connect to the VPN server and Check your anonimity.
 TheSafety
TheSafety
Anonymous VPN from TheSafety does not contain any tags.
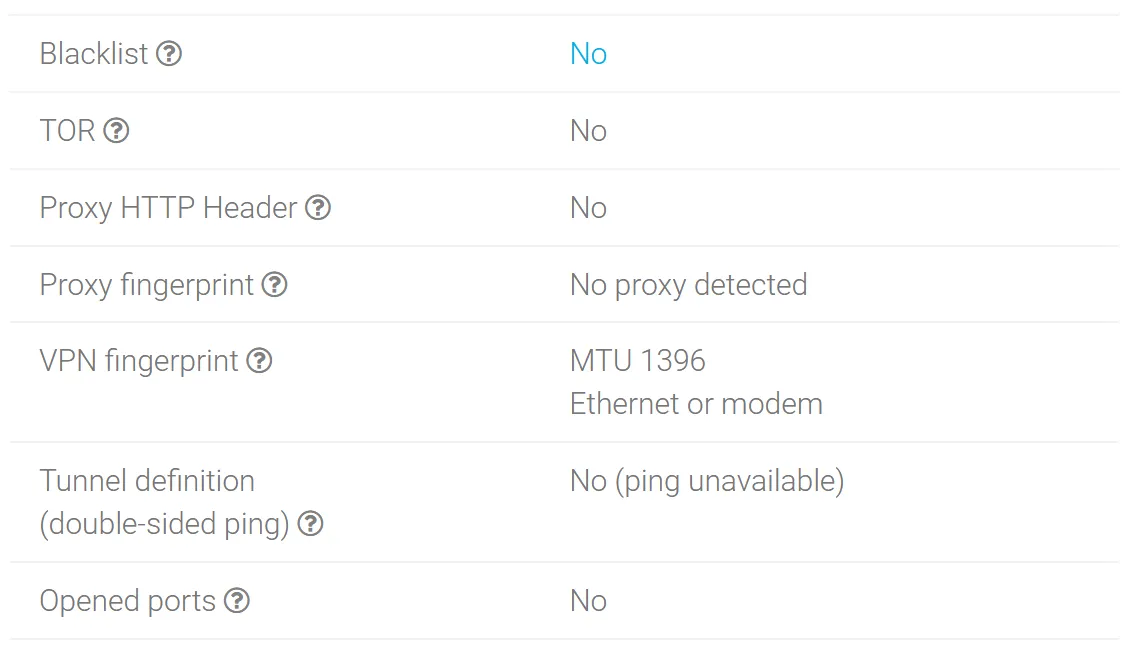
MTU 1396 (Ethernet connection has MTU 1500). The operating system is shown the same (Windows 7). This suggests that the traffic goes to the Internet directly from the VPN server (not proxied).
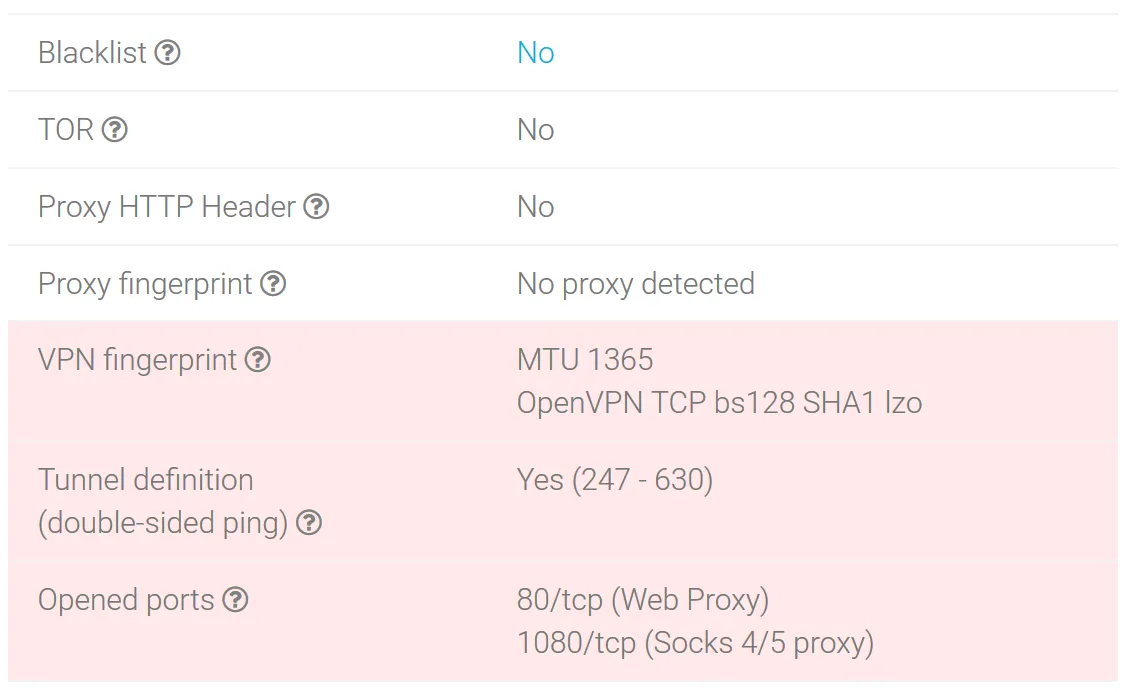
 NordVPN
NordVPN
The NordVPN fingerprints show that the tunnel is in use, the MTU 1365 parameter corresponds to the OpenVPN connection, and ports 80 and 1080 are open.
The operating system is shown the same (Windows 7). This suggests that the traffic goes to the Internet directly from the VPN server (not proxied).

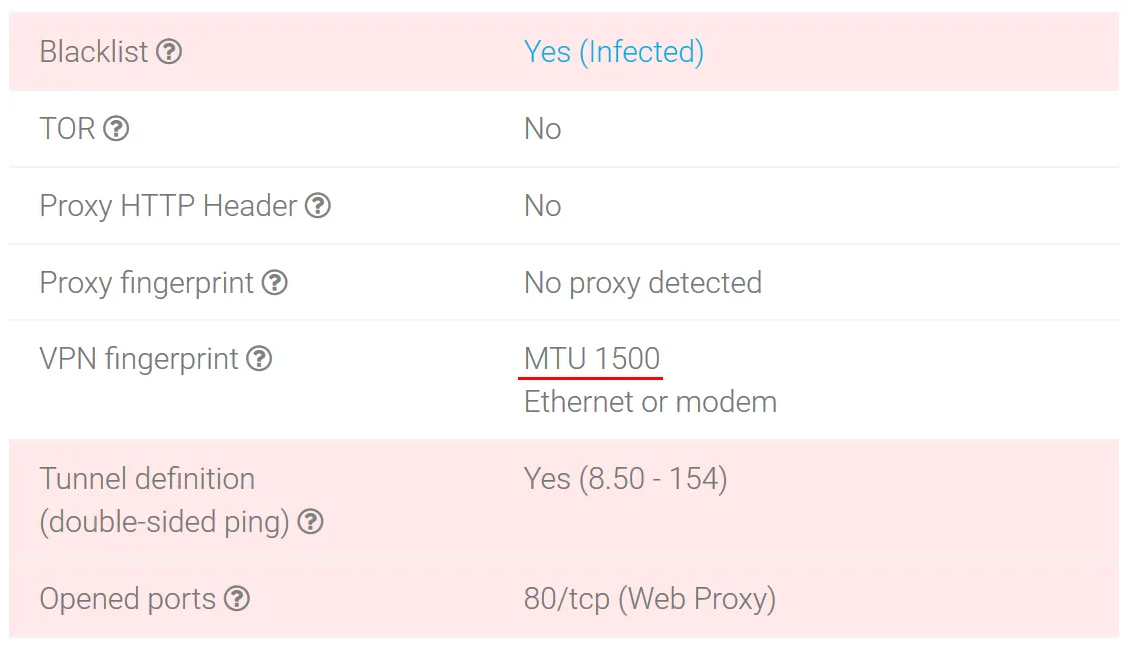
 ExpressVPN
ExpressVPN
ExpressVPN fingerprints show that the tunnel is in use and port 80 is opened.
Also note that the MTU 1500 corresponds to the Ethernet connection and is peculiar to the use of a proxy.
Proxy fingerprint was not detected because an elite HTTPS or Socks proxy is being used, which does not report the use of a proxy. In this case, all data from the VPN server goes to the local ExpressVPN proxy and only then goes to the Internet. In this case, the VPN connection may not keep logs, and the proxy will record all traffic passing through it. And then the statement that the VPN service does not keep logs will be true. Logs will lead a proxy service.
This setting is very dangerous in terms of anonymity.
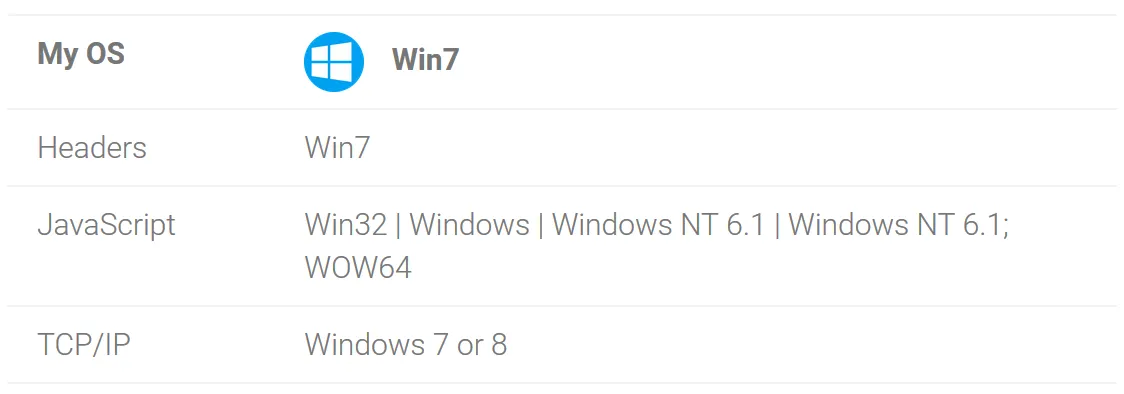
Check our suspicion of using a proxy by checking the operating system.
The browser headers and javascript show the correct use of Windows 7. The TCP/IP check shows the Linux operating system. This discrepancy indicates the use of a proxy server on Linux.
If the traffic went directly from the VPN server to the Internet, then all 3 checks would show the same operating system.
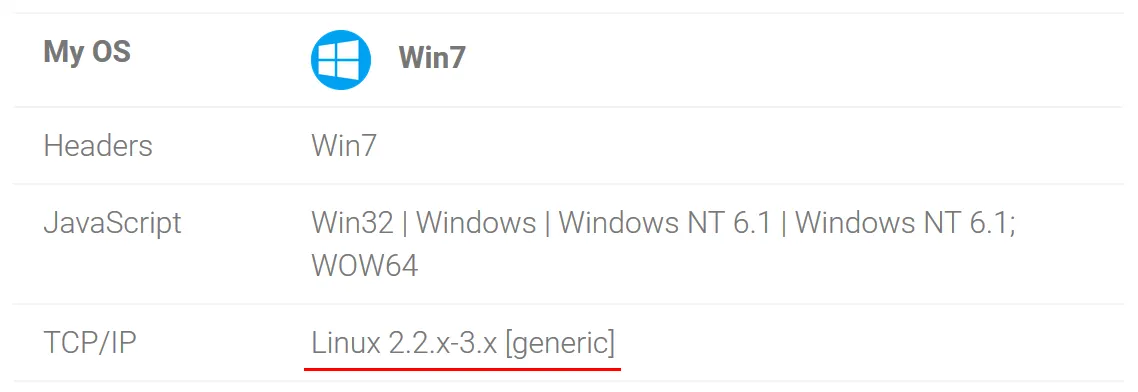
This suggests that proxy is used after VPN. And this proxy can record all traffic passing through it.
 CyberGhost
CyberGhost
CyberGhost VPN fingerprints show that a tunnel is being used, the MTU 1243 option, and ports 80, 8080 and 1723 are opened.
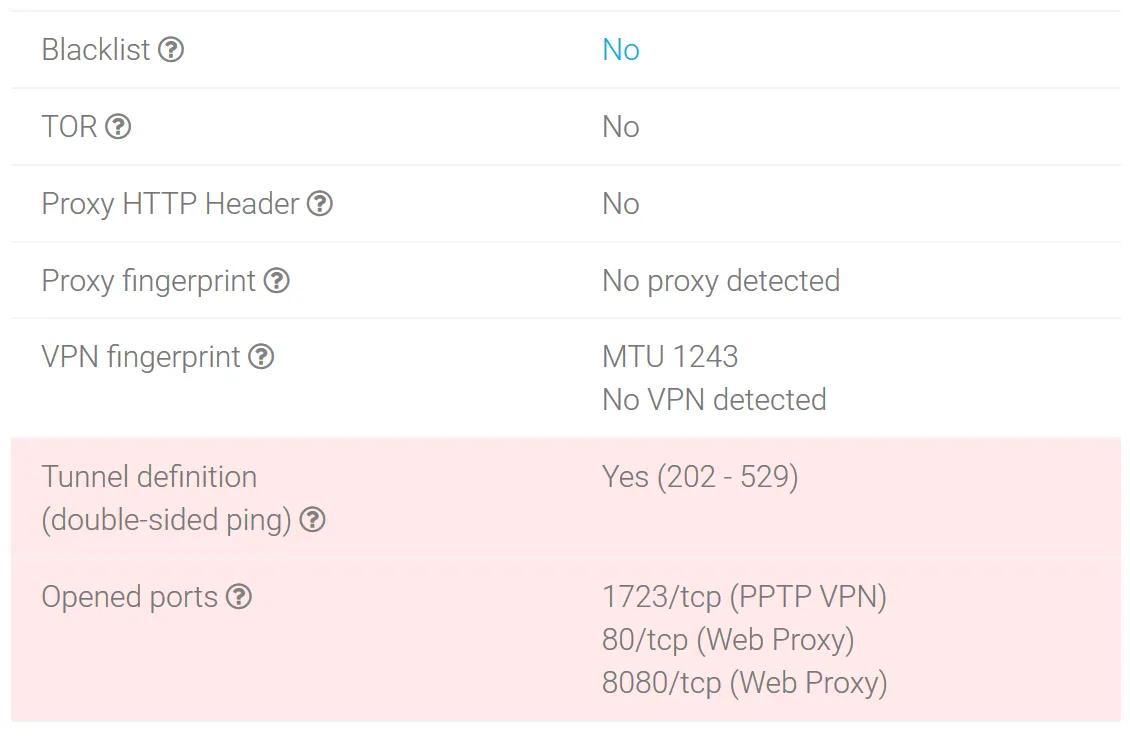
The operating system is correctly defined as Windows 7 through all checks. This suggests that the traffic goes to the Internet directly from the VPN server (not proxied).

 PrivateVPN
PrivateVPN
PrivateVPN fingerprints show that a tunnel is being used, the MTU 1380 parameter corresponds to using an OpenVPN connection.
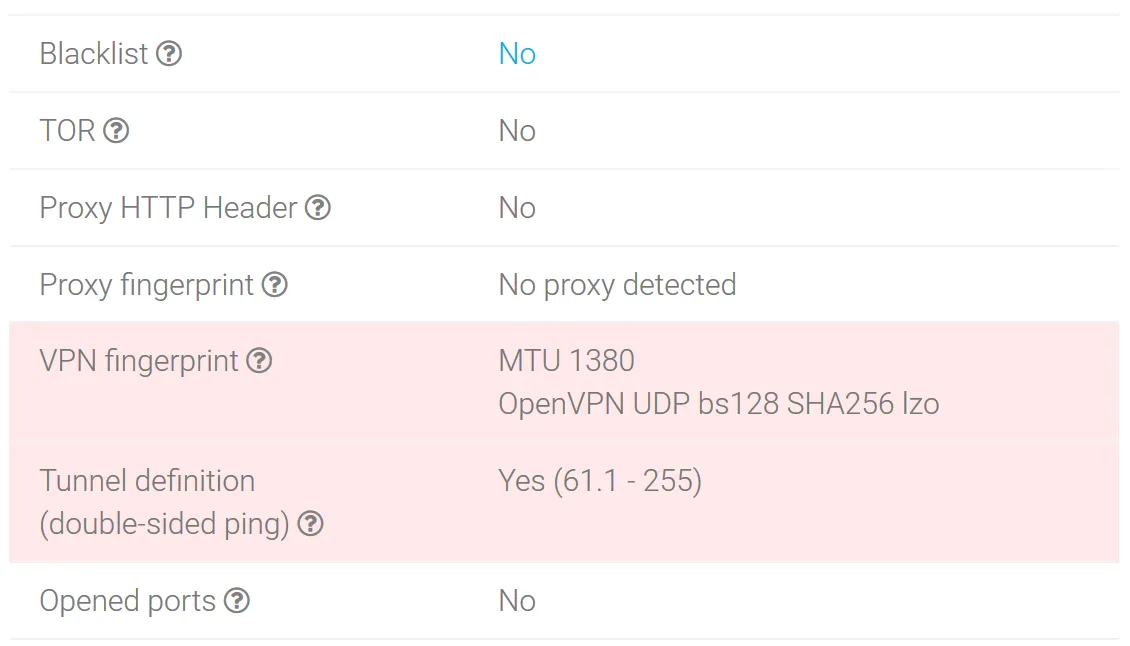
The operating system is correctly defined as Windows 7 through all checks. This suggests that the traffic goes to the Internet directly from the VPN server (not proxied).

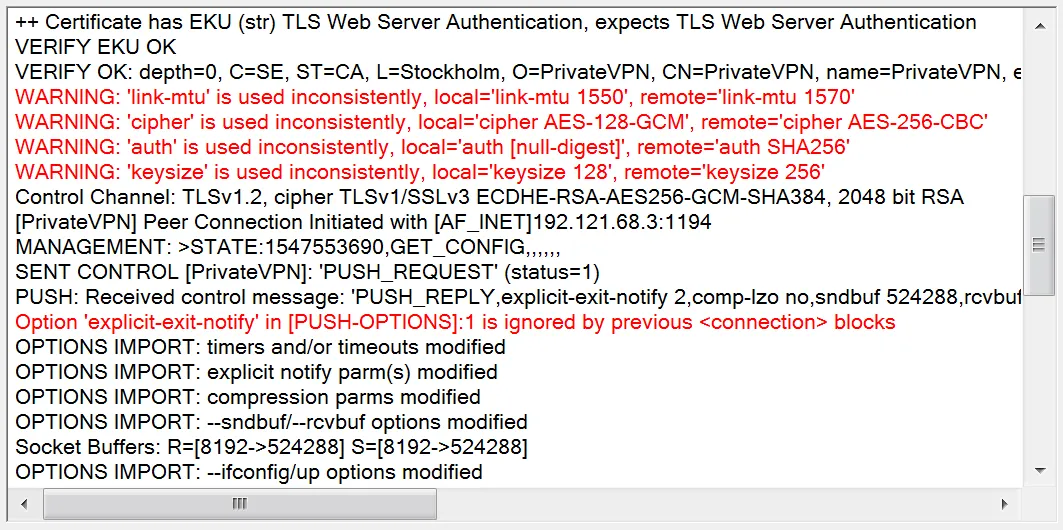
OpenVPN connection settings are not consistent with the server. Because of this, connection errors appear and an outdated encryption algorithm is used.
Double VPN
Double VPN is 2 VPN servers and the traffic between them goes sequentially. For example, you connect to a VPN server in one country and then traffic goes to a VPN server in another country. After connecting to such a bundle, you use the IP address from the second country.
This increases your anonymity, as the destination VPN server does not know your real IP address.
Obfuscate VPN traffic
There are several technologies to obfuscate VPN traffic. This is necessary when the data transfer protocol itself is blocked.
For example, in China, Iran and other countries the VPN protocol is blocked via DPI. Each protocol has its own label, which can be used to distinguish VPN traffic from visiting sites via an HTTPS connection or downloading torrents.
Traffic obfuscation is hiding traffic for another type of traffic. Usually such traffic is imitated under an HTTPS connection.
TheSafety service fully supports this feature for Standard VPN and Double VPN connections.
The NordVPN service only supports this feature for some VPN servers.
Other services do not support this feature.
Custom ports
The IANA organization assigns different ports to specific services.
For example, port 80 is used for web traffic. All websites use port 80 to display information. Port 21 uses the ftp protocol.
Different types of VPN have their own standard ports.
- OpenVPN – 1194 port
- IPSec – 4500 port
- PPTP VPN – 1721 port
If the connection goes to the standard port, then it is safe to say that this type of VPN is used.
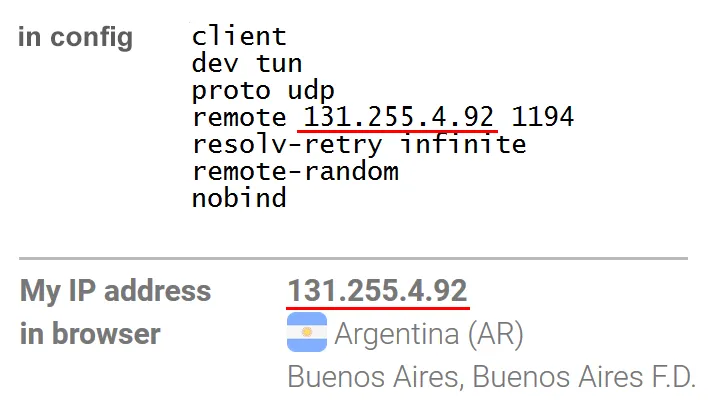
Open the OpenVPN config and find the port number in the remote line.

Connect to an IP address, not a domain
A VPN connection can be made to an IP address or domain.
To do this, open the OpenVPN config and look at the remote line. If this line indicates that the connection is made to the VPN service domain, then it is immediately clear that the user is using the specified VPN service.
For example, connecting to ar7.nordvpn.com or ar-bue.privatevpn.com unequivocally says that the NordVPN or PrivateVPN service is used.

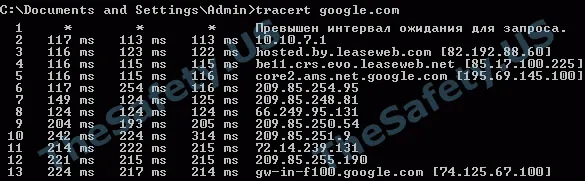
TTL change
The TTL parameter tells how many hosts passed the packet from your computer to the visited website. By this parameter you can find out how many hosts your real computer is.
To check this, connect to the VPN server and execute 2 commands via the command line.
ping google.com tracert google.com (for Windows) traceroute google.com (for Linux and macOS)
Then compare the TTL value in the ping request with the number of traceroute steps. If it matches, then the TTL parameter does not change by the VPN service.
The difference between the input and output IP addresses
A VPN connection can be made to [IP address 1], and all clients receive a different [IP address 2] output.
In this case, the ISP sees that there is a connection to IP 1, but it does not know that the client is using a different IP address on the Internet. This indirectly increases the level of anonymity.
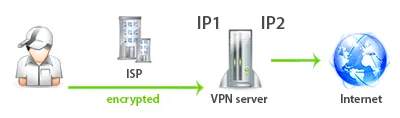
For example, NordVPN uses the same IP address in the OpenVPN config and issues the same IP address for Internet access.
Knowledge wielder is powerful
You can check all our statements yourself. We showed you the algorithm of all checks.
Think by own head and choose the best VPN service in terms of anonymity.
We have created a unique knowledge base on anonymity on the Internet and called it the ABC of Anonymity. The ABC of anonymity will tell you why on all directory sites the list of VPN services is the same.
