Review of VPN service TheSafety.US
In this review, we will analyze how the VPN service TheSafety.US provides anonymity and security on the Internet, and also tell what technologies we use for this.
Quick navigation on this page:
Review of VPN service TheSafety.US

Anonymous VPN service without logs
The most frequent question that comes to our customer service from customers: how can I check that you really do not keep logs?
Anonymous VPN service is a service that does not keep logs under any circumstances. Logs help to monitor the user, find out what sites he visited and what he did on the Internet.
VPN service TheSafety.US does not keep logs
We guarantee your anonymity and safety in compliance with our recommendations.
We can not identify each customer individually. This is anonymity. Our service is an expert on anonymity on the Internet. For many years we protect our customers.
How to check if the logs are disabled
We are often asked how it can be checked. Earlier there were no checks, how it can be done.
Thanks to our customers, we decided that it's time to create some algorithm to find out whether the logs are running on any VPN service.
The easiest way is to ask for access to the VPN server and verify it yourself. But for VPN services, this way of proving the absence of logs is dangerous.
The main problems of this method:
- It is necessary to strictly control the user's actions, since the user can upload a virus, trojan, bot.
- during the test, the user can turn on the logs himself to get any information about the active users of this VPN service (diversion from the police)
- and the biggest danger: before the check, the VPN service administrator can turn off all the logs for the user's verification time, and then re-enable it when the check is completed.
This method of verification can not guarantee the absence of logs on the VPN server.
If you give such access to all comers, then the VPN service is put under attack of its active clients. This is a gross violation of security and anonymity.
We have developed a list of questions to find out if the VPN service logs. You can ask these questions to any VPN service and analyze the answers to them. The effectiveness of this method is 98%.
Why is TheSafety.US not logging?
If any VPN service blocks your account for doing illegal activities, it means that such a service keeps logs.
We do not have data that we could issue.
We provide anonymous VPN services and do not cooperate with any organizations. We do not have any logs.
We have developed a simple system, how we can prevent users from performing certain actions while disabling logs on VPN servers.
The secret is that for VPN service TheSafety.US it is important to stop the abuse on the server. Abuse is a complaint about any actions. In the abuses, the attack time, the IP address of the attacker and other details are usually indicated. If you ignore the abuse, then the server can turn off.
Example of abuse.
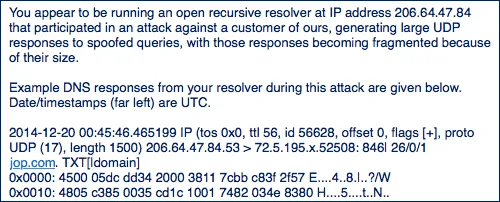
We block access to the site, which sent an abuse to the data center. Thus, no VPN server client will be able to access this site. Accordingly, unwanted actions will be stopped, and the account of this user will continue to work.
This is the main secret of providing anonymous VPN with TheSafety.US service without logs.
Is it possible to disable logs completely?
For example, it is completely impossible to disable logging on the Windows Server operating system. But there is an OS based on Linux, where it is possible to do it.
This is what the PPTP VPN server log looks like in the general system log of logs. The picture is taken from the Internet.
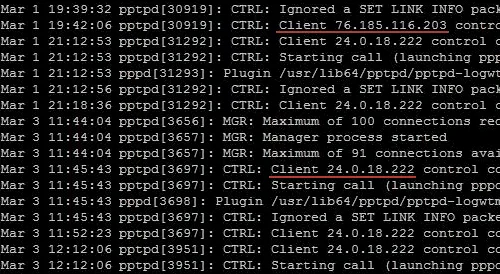
According to the log, you can find out the connection time, the real IP address of the user and the connection data.
PPTP VPN, IKEv2 VPN as well as L2TP VPN over IPSec does not have the function of completely disabling logs and continues to write the log to the general log of the system.
Be careful! If you use PPTP VPN, IKEv2 VPN or L2TP VPN over IPSec on other VPN services, then there is a possibility that such logs can be maintained. We recommend using OpenVPN connection.
On our VPN servers, we disable the syslog service, which is responsible for the common system log. Thus, IKEv2 VPN does not leave logs in the system, just as many events in the operating system stop recording.
Disabling the OpenVPN server logs is solved by adding the line log /dev/null to the configuration file.
Very fast VPN with unlimited traffic
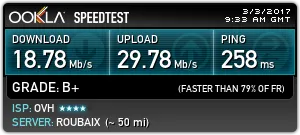
We tested the speed of our VPN connection in the Netherlands on the site speedtest.net.
Measurements were made through the OpenVPN connection using the UDP protocol. The server for testing was chosen by the site speedtest.net itself.
We were surprised by the speed of the VPN connection.
There are no speed limits for users. Traffic is not limited.
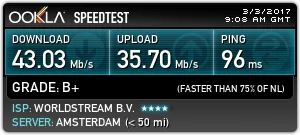
We have to warn you that the speed of the VPN connection depends on many factors and can vary depending on the busyness of your channel and the data center channel, both in large and smaller.
Strong encryption protects your data
Any browser sends an HTTP header containing specific information about your operating system, browser, language and visited sites. It is through this information that the website can find out which language you are using and show you the site page in your language.
In our review of the VPN service TheSafety.US using a special sniffer program let's find out what the HTTP header looks like without using a VPN. Your ISP knows which sites you visited.
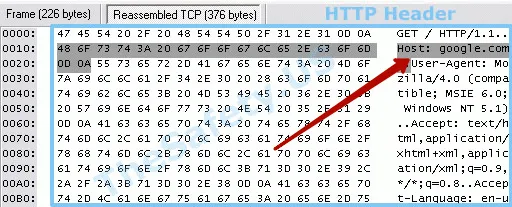
So the HTTP header looks like using a VPN.
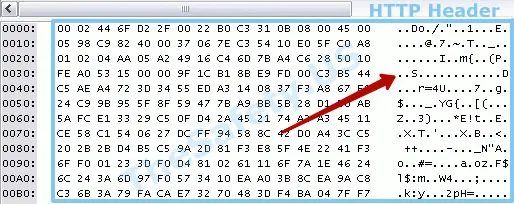
We use modern persistent encryption algorithms. Traffic can not be decrypted.
All traffic using VPN is encrypted and is a set of arbitrary characters. Thus, your ISP will not be able to find out which sites you visited under VPN.
We do not use any identification signs of connection to the VPN service in OpenVPN certificates. No domain or Email links.
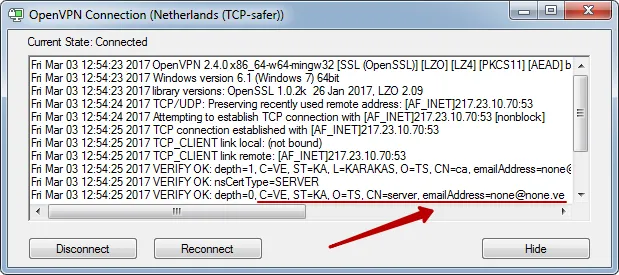
VPN fingerprints does not detect
VPN connections have such parameters as MSS and MTU. Using the standard VPN connection settings, you can calculate the standard settings for the MSS and MTU parameters and assume what type of VPN connection is used. This technology is widely used to determine the use of a VPN connection.
VPN from TheSafety.US is not defined in the VPN fingerprints section.
No one will know that you are using a VPN. Check your IP address
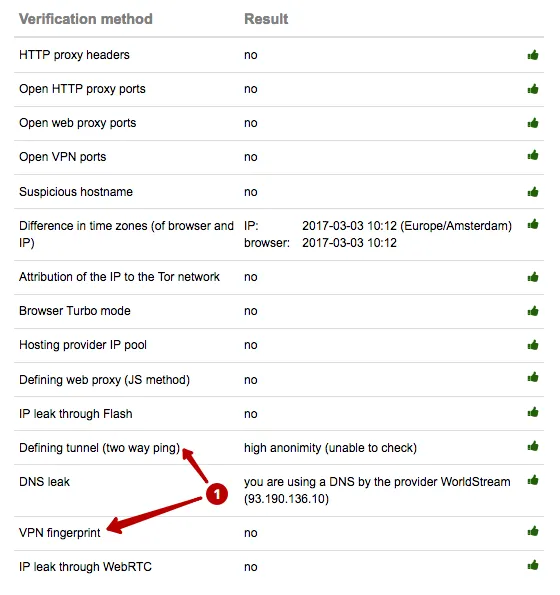
I want anonymous VPN without Fingerprint
Simultaneous connection of up to 4 devices
Connect all your devices: computer, laptop, smartphone, tablet or configure VPN on the router and then all your devices will automatically use a secure VPN connection through wi-fi.
Protection from DNS leak
DNS leak is a DNS query leak. The most common problem is found in the Windows operating system, since this is due to the processing of DNS queries. Windows sends a DNS query to all DNS servers specified in the network settings of the operating system. The local DNS server of the ISP will respond faster to the DNS query than the DNS from the VPN server due to the geographical distance.
Below is an example of DNS leak - the difference between the country of the IP address and the country of the DNS server. This indicates that there is some kind of anonymization tool.
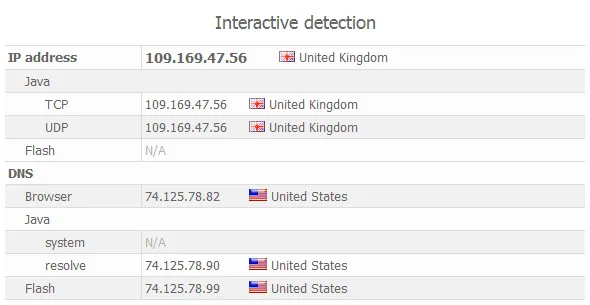
We give recommendations on how to set up a DNS service to eliminate DNS leak.
Connecting to an IP address, not a domain name
The VPN server has a specific IP address for connection. Imagine that there are 100 clients that use this VPN server. If something happened to the VPN server (blocked, seized, the equipment was broken), then you need to configure the VPN server on the new IP address and notify all clients about the IP address change.
This is not convenient for VPN services, since it is easier to make subdomains for VPNs of different countries and to change IP addresses for this domain.
If we did the same, then our customers would connect to the server in Germany this way: de.thesafety.us
The problem is that ISPs log all requests. Accordingly, the logs of the ISP will store a record stating that the user has connected to such a domain. Having entered the site, you can immediately understand that such a service provides a VPN connection and therefore this client has connected to the VPN server.
In our opinion, this can be done specifically so that you can immediately send an official request to the specified VPN service. Talk about any kind of anonymity in this case is impossible.
We use the connection to the IP address and do not bind the VPN server to the domains.
Secure Kit automatically updates IP address data. Customers who configure the official OpenVPN application are notified by email.
Internet provider will see only the connection to the IP address.
Use a static public IP address
There are 2 types of IP addresses.
- dedicated (unique) per client - only you use this IP address per time unit
- Common static on all clients
A static public IP address is an address that is permanent, does not change over time, and is the same for all users.
The plus of a static public IP address is that all clients receive the same IP address. When the abusa comes, it indicates the IP address of the attacking computer. If all clients use the same address, then it is impossible to identify a specific infringer.
If you use a dedicated (unique) IP address, the service can track you by using a unique IP address (if the service logs).
We recommend using a static public IP address on the VPN server, since only this method provides anonymity.
Not standard ports for connection
Some ISPs block the standard ports used for VPN connections. Connecting to a VPN will not be possible if you use standard ports.
For example, the standard PPTP port VPN 1723, and for OpenVPN - 1194.
Our service uses non-standard ports for OpenVPN connections. You can use our service with any ISP. Also, the non-standard port does not directly indicate that you are using a VPN.
The difference between the input and output IP addresses
Recall that the main purpose of the VPN is to change the IP address and encrypt traffic in order to hide its activity on the network from the Internet provider.
When connecting to a VPN server, your ISP will know that you have made a connection to an IP address and that information will be stored in its logs.
Be careful when using a VPN. If the VPN service gives you the same IP address at the input and output - this is a danger.
Your ISP knows that you are connected to this IP address and this data can be compared with a complaint in the abuse.
IP address - the main characteristic by which you can track the movement of data on the Internet.
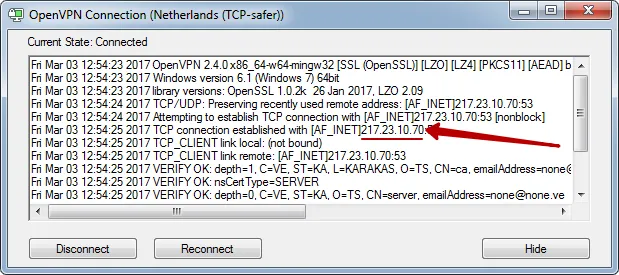
We use different IP addresses for connecting and for clients. Due to this, your ISP will not know what IP address you are using to visit sites under VPN.
You will connect to the VPN server through IP1, and be on the Internet will be under IP2. This directly increases your anonymity on the Internet.
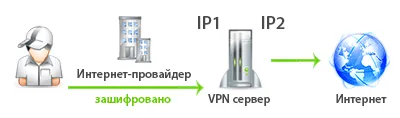
The same scheme works for us for Double VPN connections. Accordingly, 4 IP addresses change. You will connect to the first VPN server to IP1, then traffic will go from IP2 to the second VPN server to IP3. As a result, you will be on the Internet via IP4.
Force TTL
TTL is the abbreviation time to live or the lifetime of the sent packet. The standard TTL value for Windows is 128, for Linux TTL = 64.
The packet to be sent is assigned a TTL value, and this value is decreased by one by each server on its path.
For example, when you open google.com, your request packet passes through several servers (hosts), until it reaches the server on which the site is located. When the TTL value of the sent packet becomes 0, the packet is destroyed.
The main purpose of the TTL parameter is to avoid the situation when undelivered packets continue to wander the Internet forever, flooding it.
In other words, using the TTL value of the transmitted packet, you can see how many hosts the packet has passed. You can indirectly find out how many hosts your computer is in.
Our servers forcibly change this value to the default value. That is, the package seems to have been sent from our VPN server.
Using the ping command, we know the TTL value before google.com. In our case, TTL = 47.
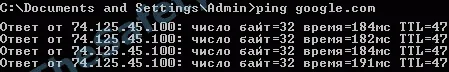
Using the tracert command, we know the number of hosts that passed the package to google.com. In our case, the number of hosts 17.
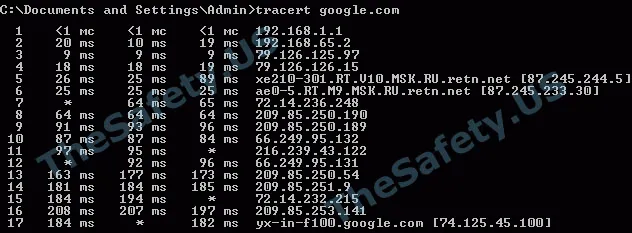
As you can see from the above examples, using the ping command, we learned that the packet passed 64 - 47 = 17 hosts. Using the tracert utility, we see that the number of hosts is also 17. In this example, the standard value TTL = 64 was taken, because the ISP on which the testing was conducted had a Linux system on the server.
The following example shows the same actions, but with a VPN server connection using our technology.
Using the ping command, we know the TTL value before google.com. It is equal to 62.
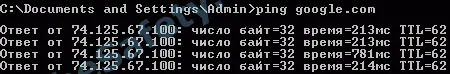
Using the tracert command, we know the number of hosts that passed the package to google.com. In our case, the number of hosts 13.
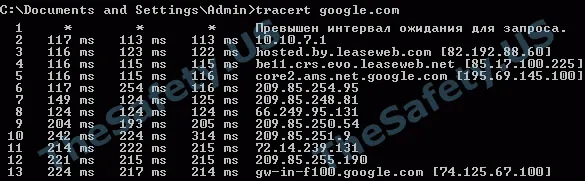
From this example, you can see that the package for the final host google.com will come with the value TTL = 62 (that is, indirectly we can say that the packet passed 64 - 62 = 2 hosts), but in fact it will pass 13 hosts.
Through our VPN connection, the resource you visit will receive erroneous data about your location.
Comments about TheSafety.US
We are experts in the field of security and anonymity on the Internet.
For all the time there is no negative feedback about our work.
We have protected all customers.
We received a lot of abuse, but no client found out about it.
We guarantee your anonymity in compliance with our recommendations.
Hey guys, I'm with you! I need your VPN
Secure Kit - convenient VPN client
The Secure Kit program will protect your Internet connection. Quick connection setup, the ability to add a connection to Favorites.
Protection from DNS leak
Secure Kit protects against DNS leak - this is the DNS query leak that most often occurs on the Windows operating system.
Blocking access to the Internet
Block Internet access using the Kill Switch feature. Secure Kit will block all Internet connections bypassing the VPN channel. No data will leak to the Internet if the VPN connection fails.
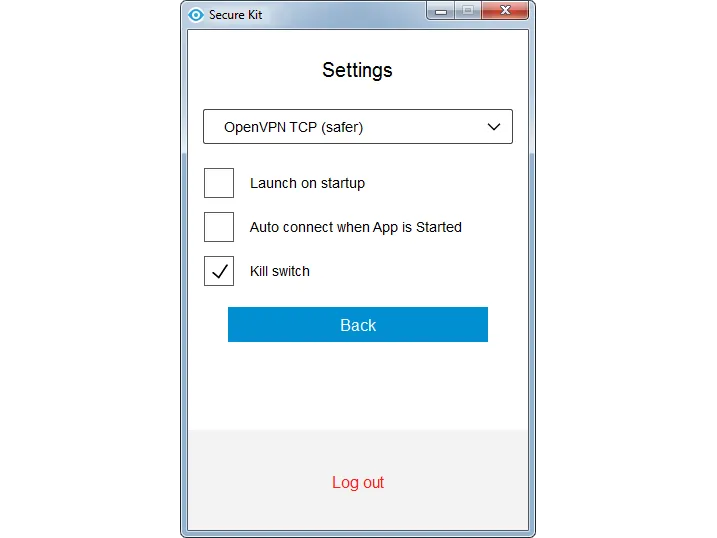
Hide the fact of using VPN
Use the Imitation HTTPS protocol, which simulates a conventional SSL connection on a 443 port. Secure Kit is able to simulate visiting a website through https. No one will know that you are using a VPN.
Cool functions! I need your VPN
The fastest VPN
We measured the speed of our VPN connection on the site speedtest.net.
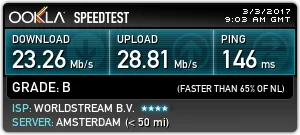
Standard VPN in the Netherlads, protocol OpenVPN UDP

Standard VPN in the Netherlads, protocol OpenVPN TCP.
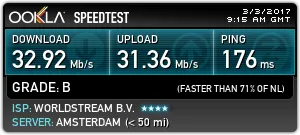
Standard VPN in the Netherlads, protocol Imitation HTTPS.
Double VPN Netherlands-France, protocol OpenVPN TCP.
Knowledge Base "ABC of Anonymity"
In 2013, we wrote the first book on anonymity on the Internet. The book consisted of 20 pages and contained basic information about ways to be anonymous on the Internet.

Now this book has been transformed into a knowledge base, where materials are collected on the topics of anonymity and security on the Internet.
Contents of the ABC of anonymity
VPN
- what is a VPN and when they need to use
- how to 100% find out if the VPN service logs
- Is it Safe to use Double VPN, Triple and Quad VPN
- what is Parallel VPN and how to use it
- setting up a VPN connection for stable operation
Proxy
- what is a proxy and how to use it
- types of proxies and where they come from
- setting up a proxy in the browser and anonymous programs
Other ways
- what is the TOR network and can it be used
- more about SSH and dedicas and how to use them
- can I use anonymizers
Browsers
- more about browsers
- anonymous browsers
- useful browser plugins
- how to check basic security settings
- do not track mode and how to protect yourself from surveillance
Virtual machines
- what is a virtual machine and how to use it
- examples of working with virtual machines on Windows and Mac OS X
- types of secure operating systems
Indirect security
- how to encrypt data. TrueCrypt Analogs
- checking the IP address in black-lists - why need to do it?
- using a DNS server
Legal issues of anonymity
- lawyer's answers to frequently asked questions
Checklist before work
- scheme that allows you to check all the main parameters in 5 minutes
- examples of setting up anonymous chains
Access to the knowledge base costs $ 149.
When buying a VPN you will get access to the knowledge base for free!
I need VPN and ABC of anonymity
